How to Spoof a Phone Number: A Comprehensive Guide
In today’s computerized world, the prominence of telephone number imitating has expanded. It can be for security reasons, privacy concerns, or just prank calling; knowing how to spoof a phone number might be fascinating but dangerous if abused. This guide will discuss various methods and consequences of spoofing telephone numbers.

What is Phone Number Spoofing?
Telephone number misrepresentation is the point at which somebody fakes their Caller ID with a specific goal of changing the number that shows up on your show. They may counterfeit it to make it appear as though they are calling from an alternate individual or association, frequently with pernicious intent.
The Legality of Spoof a Phone Number
Whether or not you are legitimately allowed to do such an activity mainly depends on where you live and why you are doing it. In some places around the world, such as America, making fake telephone numbers in order to commit fraud by impersonating governments or financial institutions is considered illegal. It can lead one to be prosecuted under the law. However, there might be times when someone needs their digits switched for legitimate reasons, like when they want privacy over anything else.
Why Do People Spoof Phone Numbers?
There are many different motivations behind people using fake caller IDs—both good-natured ones and those with evil intentions. Some folks might want to keep their safe while making calls where revealing personal details isn’t necessary at all; hence, they would opt for spoofing them instead. Conversely, this method could also be employed by individuals who wish ill upon others, such as scams, phishing attacks, or even harassment (people would harass someone anonymously).
Methods of Phone Number Spoofing
Caller ID Spoofing
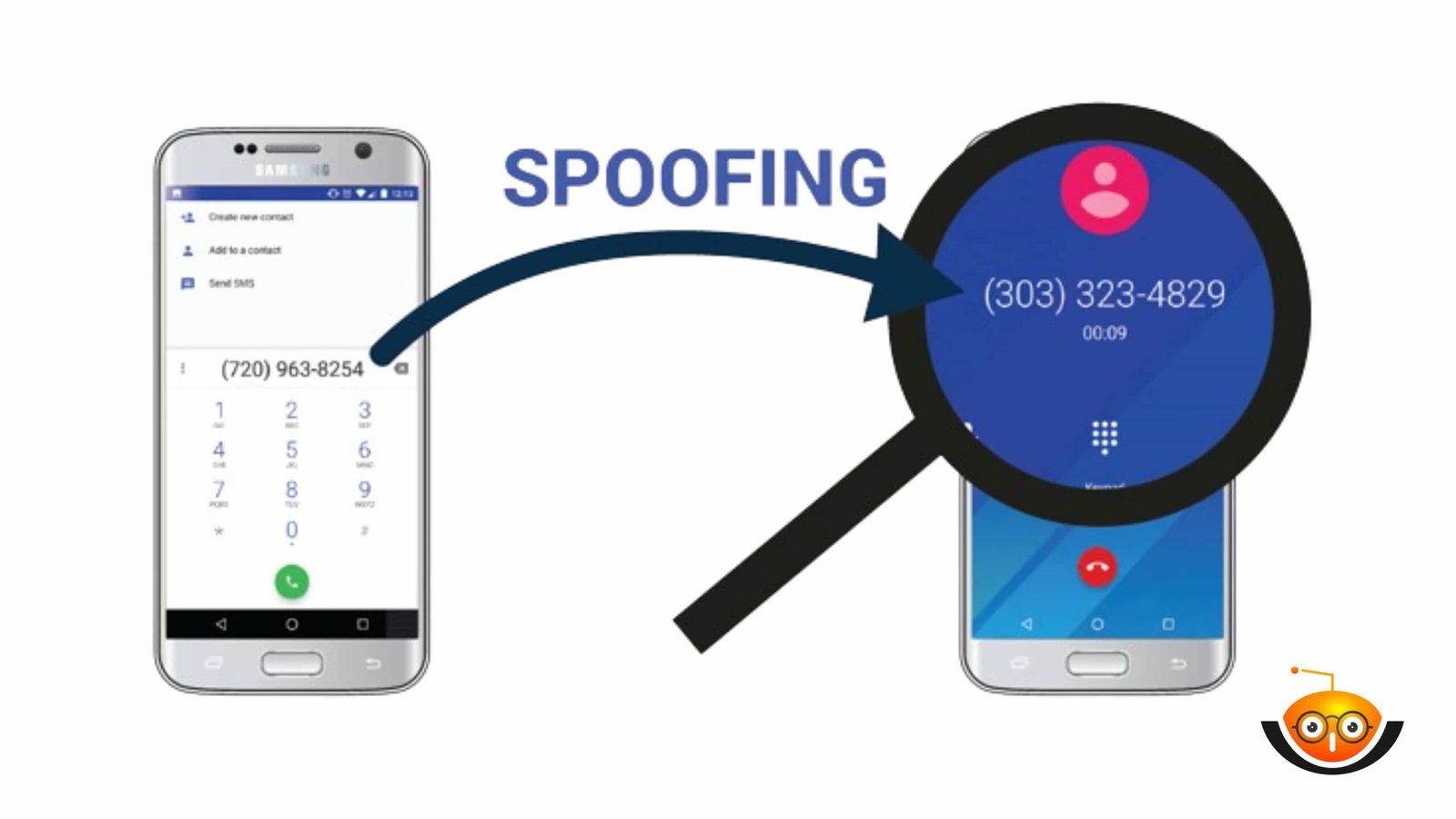
Callers have been able to change what appears on the caller ID when they call since phones became digitalized; these days, its popularity knows no bounds thanks largely to smartphones’ wide usage across practically every age group imaginable but also because many other devices now offer similar features too! A person can manipulate the caller ID information displayed during a phone call with ease. ‘Caller ID Spoofing’ is the term used for this. Although not always malicious, as there are times when people may want to hide their identity from the person they are calling, this is why they change what appears on the receiver’s screen.
How Caller ID Spoofing Works
Usually, when someone calls you, their number pops up on your phone along with other important details like their name if it’s saved in your contacts or any personal information attached to them through third-party apps such as WhatsApp, etcetera; this happens because of a system called ‘Caller Identification’, which shows different pieces of information about an incoming call including where it might be coming from and who could have made it then sends these details straight to your device. However, with caller ID spoofing, the displayed information can be manipulated so that instead of seeing one thing, another shows up instead, thus giving off a different impression altogether.
Uses of Caller ID Spoofing
There are various legitimate uses for caller ID IDoofing, including but not limited to the following;
Protection of Privacy: Some individuals may wish to keep certain things private and would rather not share their real numbers when dealing with strangers or businesses whom they don’t fully trust; hence, they opt for fake ones instead.
Branding Purposes: To create uniformity among employees while at work, companies could use this technique, whereby all calls made by staff members display only one recognizable telephone number regardless of who is actually placing the call. This would ensure that customers know exactly what brand message is being communicated across all channels.
Anonymity: Caller ID spoofing can still be used to remain anonymous when reaching out to someone, whether for personal or professional reasons.However, caller ID spoofing also carries with it risks and ethical concerns.
Risks and Ethical Concerns of Phone Number Spoofing
While fake caller recognition has legitimate uses, there are many dangers and ethical considerations tied to it. These encompass the following:
Fraud and Scams: ThiSwindlers use this method to get people to respond or give their data to them. They can pose as a government department, bank, or other reputable organization to obtain professional or financial details from individuals.
Bullying And Harassment: Spoof calls permit offenders to make anonymous threatening phone calls, making it difficult for victims to report such cases.
Illegal Activities: In certain nations, mimicking someone else’s use of these gadgets is viewed as unlawful, particularly if it involves distortion.
2- Voice over Internet Protocol Services (VoiP)
In expansion to changing customary phone specialized strategies, voice-over-internet protocol (VoIP) services give a simple way for clients to change their numbers. Some VoIP providers offer features that let subscribers manipulate the calling party identification parameter (Caller ID). This effectively spoofs their phone numbers. Here’s How VoIP Can Be Used For Phone Number Spoofing:

Using Caller ID Settings: Many VoIP providers allow users to change what appears on the recipient’s phone when they call them via the account settings or user interface of the service. They achieve this by enabling people to select an alternative number associated with their accounts as a default outbound caller ID so that it shows up instead during outgoing calls made from those particular systems; hence, it appears as though it originated from another line altogether even though dialed through one system only.
Third-Party Applications: In addition to built-in caller ID settings, some voice-over-internet protocol services provide third-party applications or integrations specifically designed for phone number spoofing. These apps offer additional features and options, such as changing one’s voice during conversations or recording them, among other things. Users can download such programs from app stores or directly from the provider’s website for more advanced capabilities when it comes to spoofing caller ID information.
Here are two top third-party apps:
Spoof Card: This is a well-known application that enables users to change their caller ID information when making calls. It allows people to alter the number displayed on someone else’s device, change their voice in real-time during calls, record conversations, and much more. SpoofCard is available for both iOS and Android devices.
Burner: Another popular app widely used by many individuals. Burner provides temporary phone numbers for various purposes, including spoofing caller ID information while making outbound telephone calls, among other features as well.

You can generate disposable lines whenever required, then select any of these temporary contact points before initiating any form of communication with others through them, which might involve giving away personal details unnecessarily. Burner can be downloaded onto iPhones or iPads running iOS 11 onwards, plus Android smartphones running Android 7 onwards.
Online Platforms
Some websites dedicated to VoIP communication also allow phone number spoofing as a feature. Such platforms usually have an easy-to-use interface where you can change your caller ID information by simply entering the desired number you wish to display when making calls. Available from a device with an internet through web browsers, this makes it convenient for individuals wanting to spoof phone numbers without having to install any additional software.
Protecting Yourself Against Phone Number Spoofing
1. Activate Call Blocking Features
Most current phones have a call-blocking feature. This feature allows blocking some specific numbers or types of calls (like unknown or private). Switching on these features will decrease the number of fake calls received from unwanted or suspicious sources.
2. Learn and Teach
If you want to fight phone number spoofing, you should be aware of this problem. Please find out more about it yourself and share your knowledge with others. Tell them about possible scams and frauds that may come via spoofed calls. Ask colleagues, friends, and kin to double-check when answering unrecognized numbers and identify callers if they hesitate.

3. Security Software Installing
To detect and prevent spoofed calls, an individual can install reliable security software that works on their PC or smartphone. There are plenty of such products in the IT market, many of which possess call screening options for incoming ones analysis on presence signs showing fraud attempts or fake calling identity verification while protecting devices proactively through security software decreases chances of falling into phone number spoofing trap.
4. Report Strange Behaviour
Once someone has received a fraudulent call – report it! Let competent authorities deal with these issues by reporting any illegitimate activity involving telecommunication systems where several countries do have dedicated agencies dealing against fraudsters. Hotlines too. In doing so person helps officials dig deeper into cases related not only to Scamming but also Caller ID Faking, among others, thereby enabling them to take necessary actions against individuals engaged themselves perpetrating acts using fake caller IDs alongside other crimes associated with this particular offense.
Conclusion
In summary, the act of falsifying phone numbers might appear as just another joke or method for guarding one’s privacy; however, ethics alongside the legality behind such action cannot be underestimated at all levels within society today. Hence, people must learn how best they can impersonate telephone numbers without causing harm either physically, emotionally, spiritually, mentally, financially, socially etcetera following given instructions, thus minimizing risk factors involved during undertaking this exercise.











