Connect to Hotspot Without Password: Easy Guide
Today’s world of hyper-connectivity has made the internet a necessity from being a luxury. Whether it is for work, pleasure, or socialization, one needs to be connected all the time. But what happens when you desperately need it and there are no Wi-Fi networks around you? Or when someone has a hotspot, but you need to know their password? here is easy guide Connect to Hotspot Without Password.
What are Hotspots?
Hotspots are physical locations that provide wireless internet access through Wi-Fi technology. They are usually found in public areas such as airports, libraries, hotels, or cafes where users can connect their devices.”
Types of Hotspots
Public, private and personal hotspots are some forms in which they come. Anyone within range can connect to public ones, while private ones require authentication before use. Personal ones are created by individuals using their smartphones or other devices to share their internet connection with others.
Mechanism
They function by establishing a wireless connection between a user’s device and a hotspot access point. The access point is commonly attached to a router or modem that provides connectivity to the Internet. When a device is linked to it, data passes via this access point to the web, enabling the user to browse pages, stream media, etcetera.
Advanced Methods Connect to Hotspot Without Password
Exploiting Vulnerabilities:
This technique entails finding weak spots on either security protocols used in setting up Wi-Fi networks themselves; alternatively, they may target gadgets linked up to these systems.

Hackers could exploit outdated firmware versions, default configurations settings, or known flaws that exist within particular brand names’ routers, amongst others, so as to gain unauthorized entry points into such networks without knowing the passwords required for WPA2 PSK encryption type used here (Advance Encryption Standard).
To do this, attackers can utilize diverse tools and techniques, such as port scanners and vulnerability scanners until they identify vulnerable areas against which attacks will be launched. Thus, intruders can gain network access without necessarily having a WiFi password.
Using Third-Party Tools:Connect to Hotspot Without Password or wifi
These are software applications or programs created to aid in hacking or gaining unauthorized entry into Wi-Fi networks. Most of these tools come packaged together, thereby automating scanning for vulnerabilities, exploiting weaknesses, and connecting with Wi-Fi without necessarily needing passwords.
Network sniffers, password-cracking tools, and WiFi hacking apps are among others that can be classified as third-party applications. Although some of them may have legitimate purposes, it is common practice among hackers to utilize these applications when conducting their malicious activities.
Two top-notch third-party tools commonly used for Wi-Fi hacking are:
Aircrack-ng:
For assessing someone’s hotspot or Wi-Fi security, Aircrack-ng is a powerful suite of tools used in testing Wi-Fi network security. It consists of packet-capturing toolkits, packet analysis utilities, and password-cracking modules. Aircrack-ng can also monitor Wi-Fi traffic, launch attacks against WPA/WEP networks, and crack down on Wi-Fi passwords through dictionary or brute force attacks.
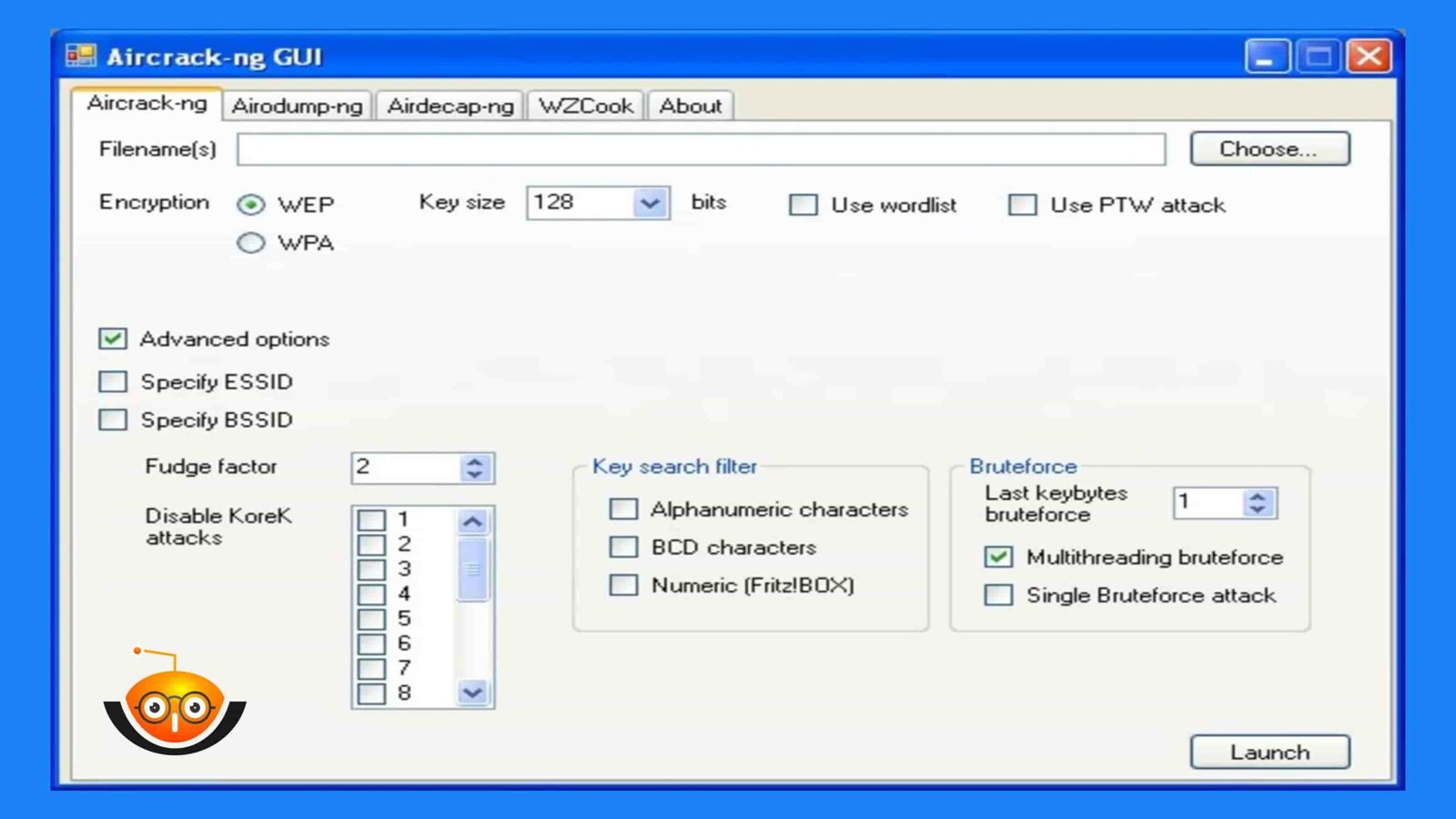
It’s a highly effective tool for examining wireless networks’ reliability. Still, it should only be used ethically, such as by network owners to check if their systems are secure enough or during authorized vulnerability assessments within organizations where regulatory compliance standards like HIPAA, etc., have mandated this kind of testing.
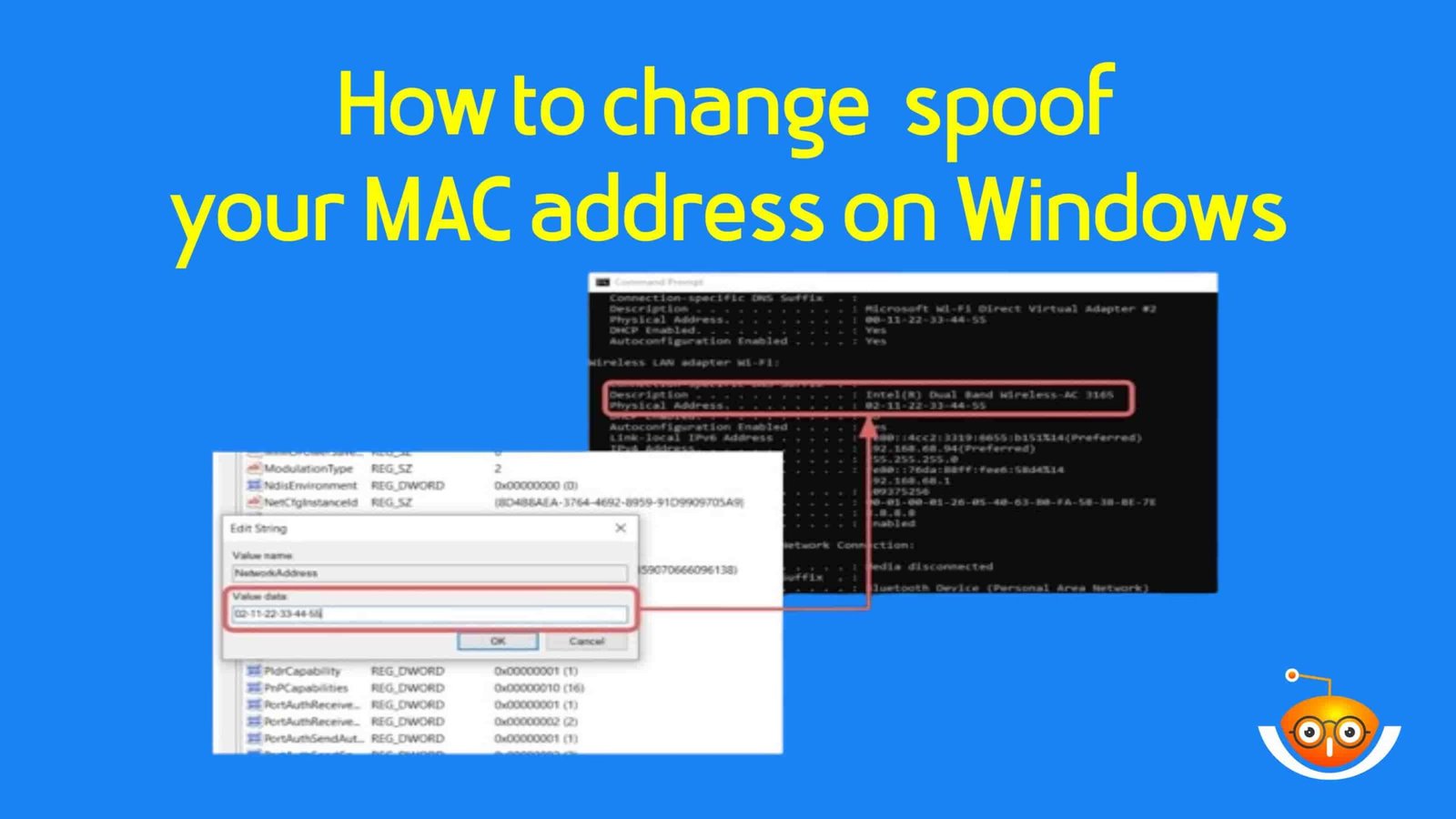
MAC Address Spoofing: Connect to Hotspot Without Password
This involves changing a device’s Media Access Control (MAC) address so that it impersonates another to bypass certain restrictions imposed by Wi-Fi networks. Every network-connected gadget has an exclusive MAC ID, which is utilized to identify and interact with other devices over such (LAN) Local Area Network connections.
Attackers can make the Wi-Fi access point believe they are an authorized device without a password by spoofing or changing their device’s MAC address to match one of those allowed on the network. This technique is often combined with other hacking methods to gain unauthorized access to WiFi networks while remaining undetected.
Find out Your MAC Address:
Before you start spoofing your MAC address, you should know your original MAC address. You can find this in the network settings normally, or if all else fails, try commands like “ipconfig /all” in Windows and “ifconfig” in Linux.
Choose which MAC Address to Spoof:
Decide on the MAC address that you want to use for your spoofed device. It can be random or from another device that is permitted to connect with the wireless network.
Spoof Your MAC Address:
Either use tools designed specifically for spoofing MAC addresses or manually change them yourself through your device’s network settings. Follow instructions given by these programs; otherwise consult documentation of devices being used when configuring it manually.
Connect To The Wireless Network:
After successfully spoofing your MAC address, try connecting as usual. Your gadget will now appear connected on WLANs/Wi-Fi networks under the spoofed physical/MAC address.
Authenticate if Required:
If there is any form of authentication needed, such as entering passwords or accepting terms, then complete them before getting connected else, wait for confirmation – now it should say connected somewhere around there. Still, I’m not sure since each operating system displays information differently even though they are doing the same thing at this stage, so follow the prompts shown on the screen, plus keep an eye out, my friend!
Traditional Methods
Requesting the Password:
Ask the hotspot owner or administrator for the password. It’s a direct and effective way to gain access, especially in private or controlled environments.
Social Engineering
Manipulate individuals into sharing the password through psychological tactics. While effective, it’s unethical and may have legal consequences if misused.
Guessing the Password
Attempt to guess the password by trying various combinations of characters. This may take a while, but it is a good method when others are not possible.
Risks When Connect to Hotspot Without Password
Connecting to hotspots involves many risks, such as security and legal issues. It is important to know these risks so that they can be avoided and one can have a safe and legal internet browsing experience.

Security Risks
When you Connect to Hotspot Without Password, of someone wifi, there is a big risk to security. Cybercriminals, who may intercept data by hacking into these systems, often target them. Without encryption or any other type of safeguarding, your passwords, financial records, and private information could easily be hacked.
Legal Considerations
Unauthorized use of someone else’s WiFi can have serious legal implications. It may violate privacy laws and new firms of service agreements. The possible penalties for these acts differ by locality but may involve fines, civil litigation, or potentially even criminal prosecution. This underscores the, importance of others’ privacy and seeking legal WiFi networks.
conclusion
Though the thought of accessing another individual’s hotspot minus a password might appear attractive at times when everything else has failed, it is necessary to handle such situations carefully while considering other people’s privacy and safety. Also, rather than resorting to potentially unethical acts, you should seek consent or find WiFi networks because through prioritizing morality within ourselves, we will foster an online environment that is more secure for everyone.